Policies and Egress Policies
What are Policies?
About Policies
A policy defines how groups can interact. Groups are connected via policies, which form the foundation for BlastShield access control and segmentation management.
Each policy will have two sets of groups - "From" and "To".
The "From" set is one or more source groups.
The "To" set is one or more destination groups.
There is no limit to the number of groups in a given policy.
"From" Groups will have access to "To" Groups within the policy.
"To" Groups will not have access to "From" Groups within the policy.
Groups can be in one or multiple policies simultaneously.
Note
Policies are directional, so that you can control the direction in which connections may be initiated. Typically for remote access use-cases your policy would be from the "user group" to the "server group" so that users may start connections to the servers, but servers cannot start connections to users. You can create bi-directional permissions by using two policies.
Examples of Policies
Example 1
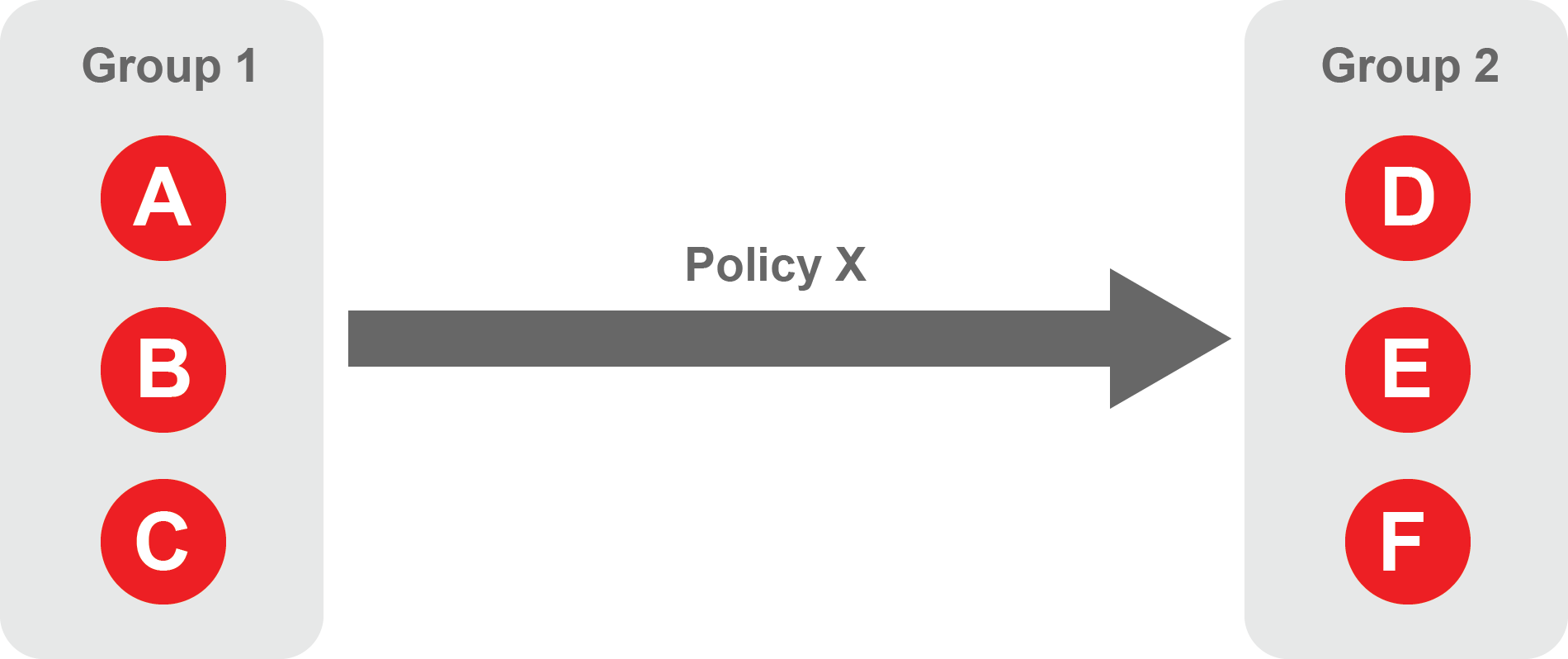 |
Group 1 contains three endpoints - A, B, and C.
Group 2 contains three endpoints - D, E, and F.
Group 1 endpoints can access Group 2 endpoints.
Group 2 endpoints cannot access Group 1 endpoints.
These groups are connected by a policy - Policy X
Example 2
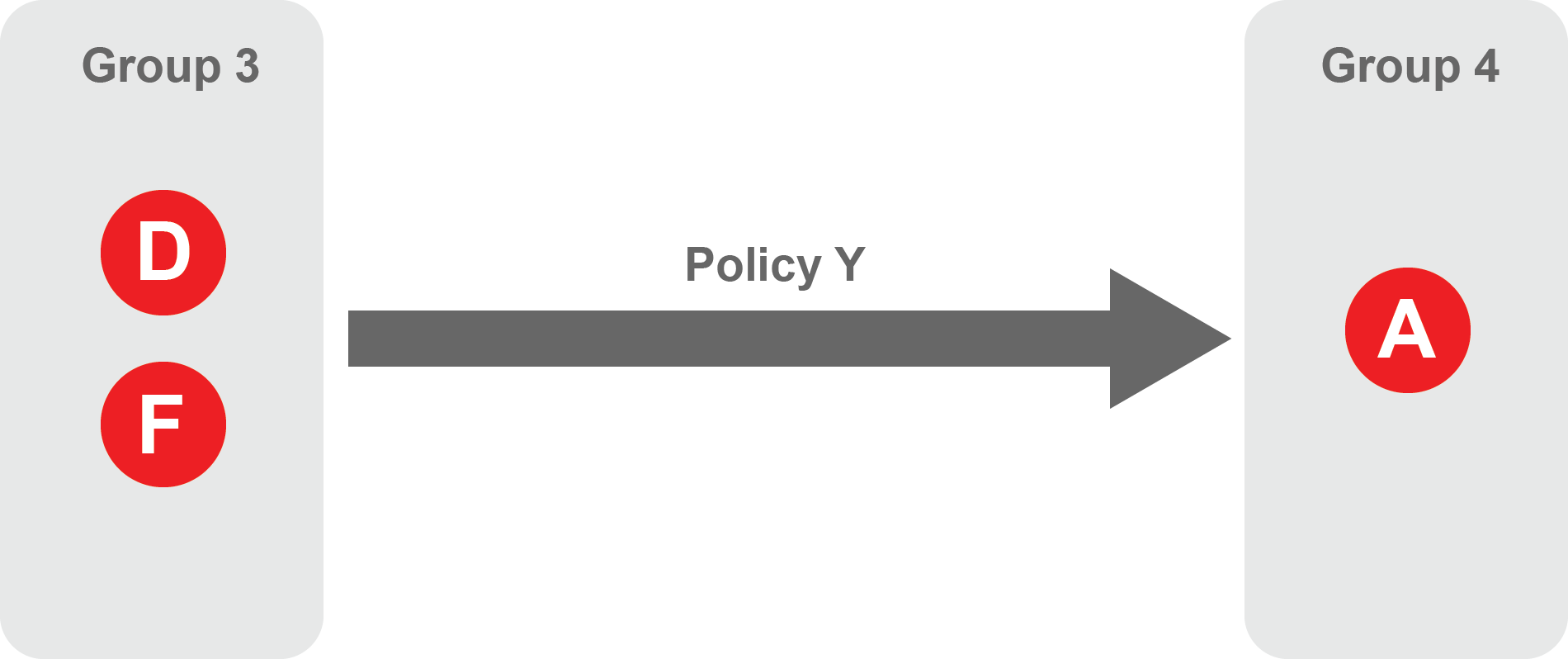 |
Group 3 contains two endpoints - D and F.
Group 4 contains a single endpoint - A.
Group 3 endpoints can access Group 4 endpoints.
Group 4 endpoints cannot access Group 3 endpoints.
These groups are connected by a policy - Policy Y
Note
Notice that endpoint A is associated with multiple groups and multiple policies.
What are Egress Policies?
Egress policies allow you to control external network access for Gateway endpoints which are isolated behind a Gateway. This enables endpoints to connect to external entities, for example to download a software update or to connect to an NTP server.
Examples of Egress Policies
Example 1
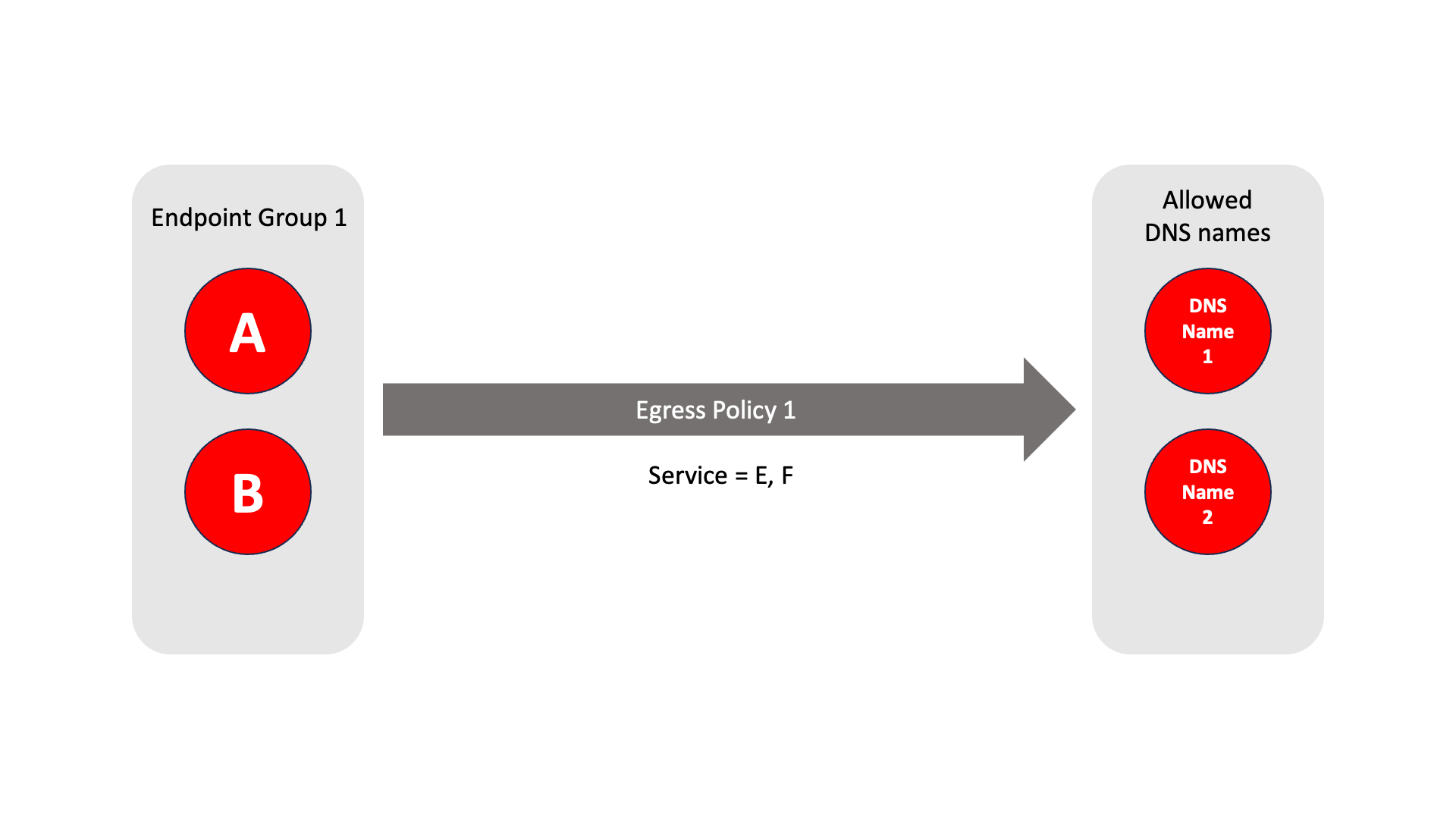
Endpoint Group 1 contains two endpoints - A and B.
The allowed DNS names contain external DNS names 1 and 2.
Endpoints A and B can resolve and connect to DNS names 1 and 2.
The allowed services are E and F.
This relationship is defined by Egress Policy 1.
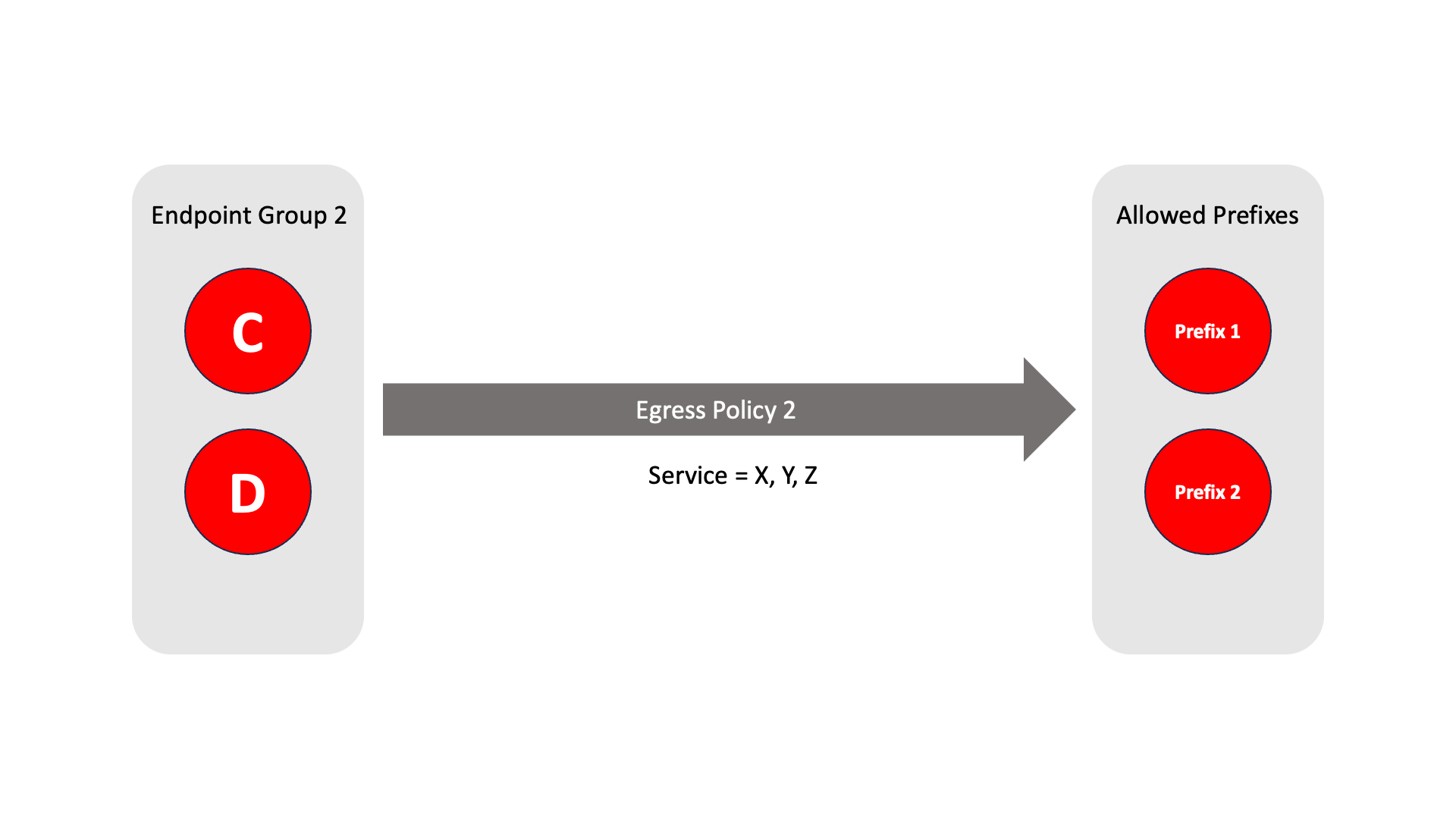
Example 2
Endpoint Group 1 contains two endpoints - C and D.
The Allowed Prefixes contain external network prefixes 1 and 2.
Endpoints C and D can resolve and connect to network prefixes 1 and 2.
The allowed services are X, Y and Z.
This relationship is defined by Egress Policy 2.