How BlastShield Provides Micro-Segmentation
BlastShield™ enables micro-segmentation of users, Host Agents and Gateway endpoints. Micro-segmentation is combined with zero-trust policy enforcement for secure remote access using a software defined perimeter (SDP) model.
Micro-segmentation Groups
A BlastShield™ network enforces micro segmentation of users, and protected assets (Host Agents and Gateway endpoints) at the network layer. BlastShield™ uses groups to define the logical grouping of nodes for micro segmentation. A group is a logical collection of endpoints, agents and/or users that are grouped together. Groups in BlastShield™ are independent of the underlying network segmentation which gives you flexibility to configuration micro-segmentation without having to rely on complex VLAN configuration. Groups are connected via policies, which form the foundation for BlastShield™ access control and segmentation management.
You can combine Host Agents and Gateway endpoints in the same micro-segmentation group, and they may be a members of multiple groups. Host Agents may be installed on Linux/Windows.macOS hosts, cloud endpoints and VMs. Gateway endpoints may be Linux/Windows.macOS hosts, cloud virtual instances, VMs, IoT devices, automation/OT systems and controllers, PLCs, IP Cameras or any IP addressable device.
Policy checking and enforcement of micro-segmentation
Micro-segmentation is enforced on a connection by an evaluation against the available policy or policies. BlastShield uses zero-trust principles, so if a connection matches a policy then it will be allowed, and connections which do not match a policy are dropped. Furthermore, any connection attempt from a non-BlastShield™ user to a BlastShield™ node will fail the cryptographic authentication check and the packets will be dropped.
A policy simply defines that a node or nodes in a source group may initiate connections to a node or nodes in a destination group: it defines a “From” group of nodes, a “To” group of nodes, and the direction of allowed connections. The policy checking and enforcement is done by both the client and the Host Agent or Gateway endpoint. This is done independently of the Orchestrator for increased efficiency to provide the optimum performance. The following examples illustrate how micro-segmentation is be implemented.
Example 1 Micro-segmentation of remote access users
In this example, micro-segmentation is used to isolate the resources required for corporate remote access users. The remote users require secure access to the finance and HR systems, where the former is located in a data centre and the latter is running as a virtual instance in a private cloud provider.
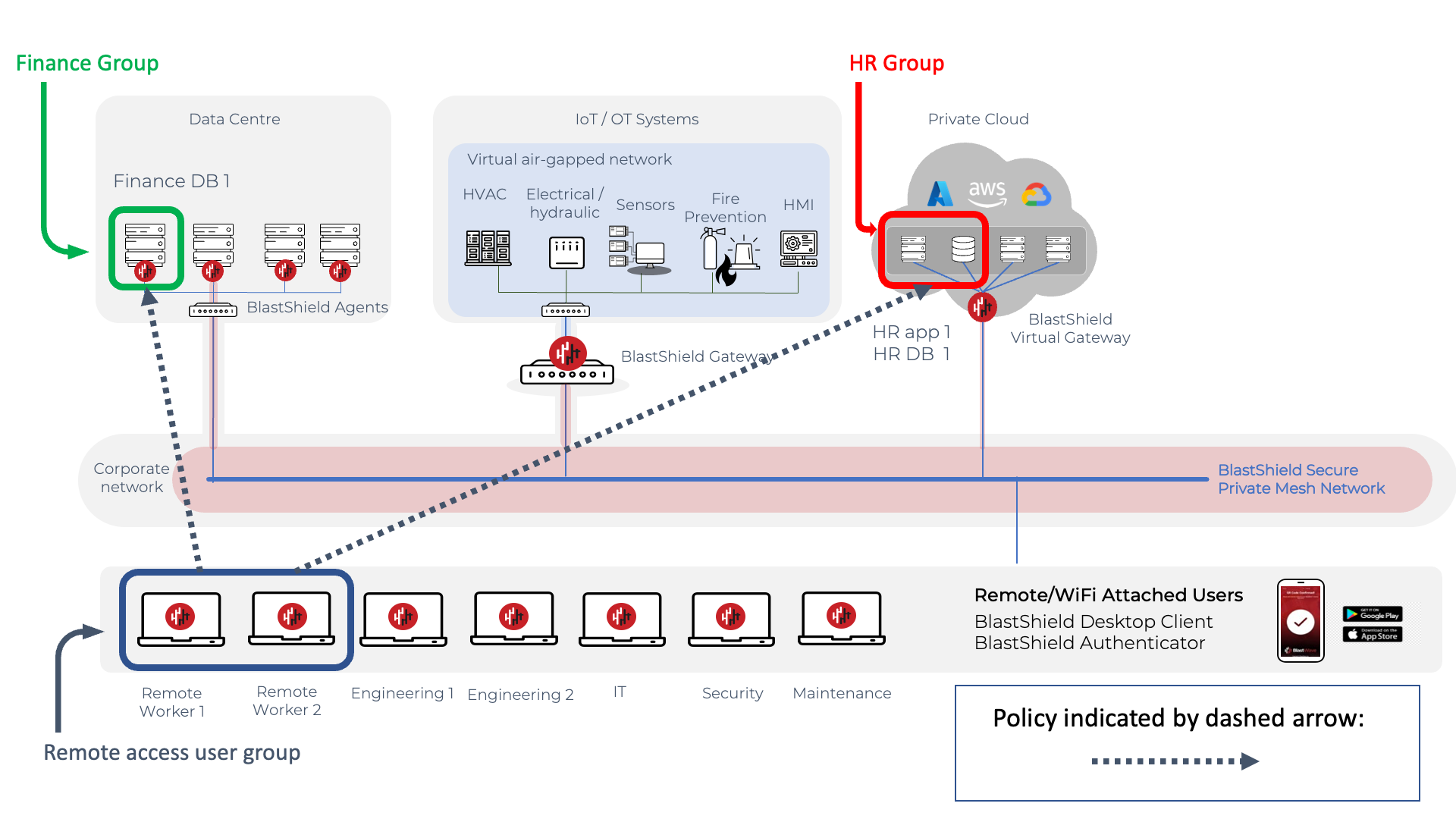
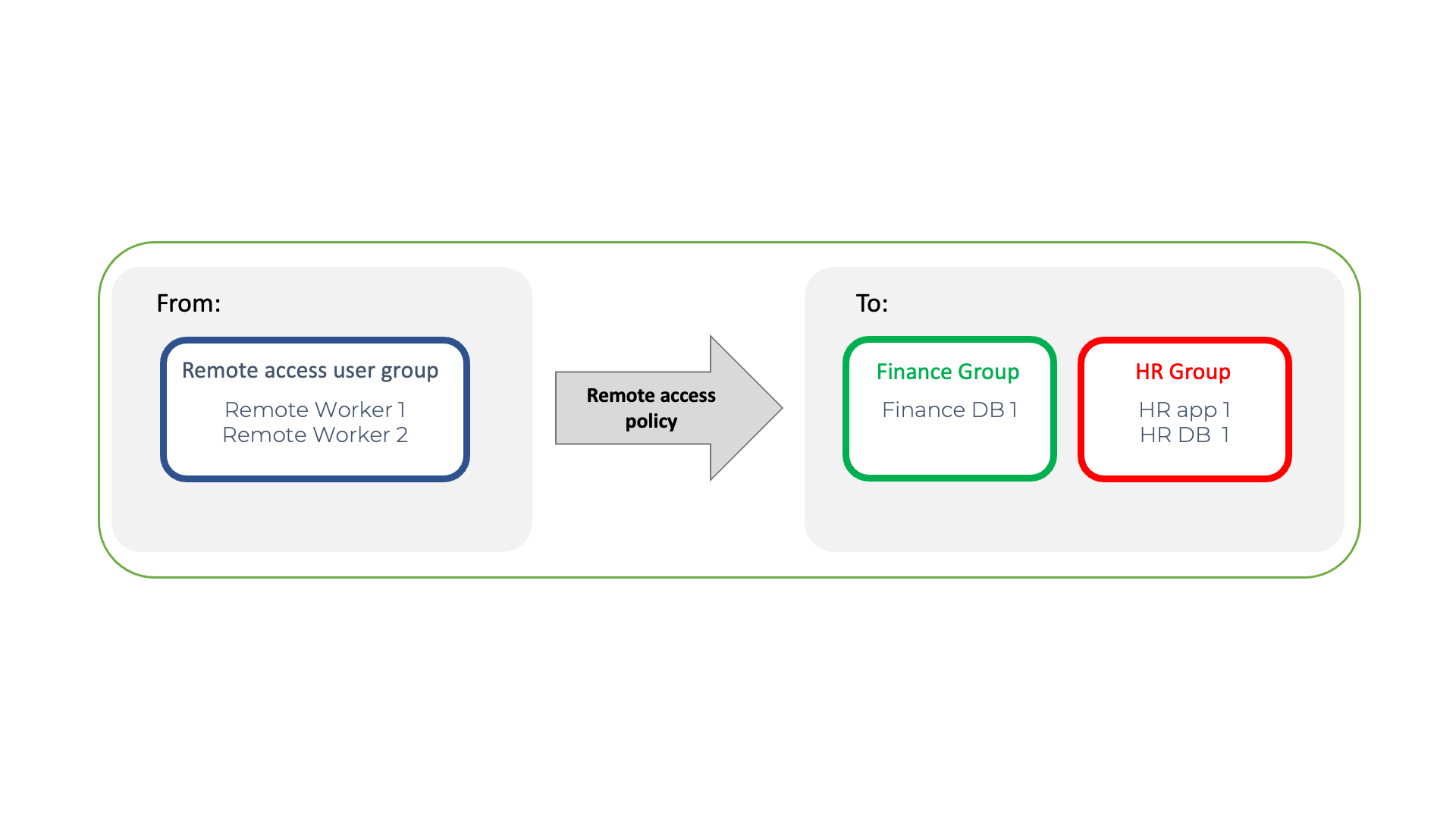
The policy for this example is shown below. Both the finance and HR systems are defined in separate dedicated groups, to segment them from all the other systems which the remote users are not authorised to access. Similarly, the remote users are defined in a group and these three groups are used in a policy to provide for micro-segmented remote access. The policy allows the remote users to access the finance and HR systems, but they may not access any other system.
Example 2 Micro-segmentation of engineering users
In this example, micro-segmentation is used to isolate the resources required for the engineering team. They require secure access to the test and build systems, where two test hosts are located in a data centre and the build host is running as a virtual instance in a private cloud provider.
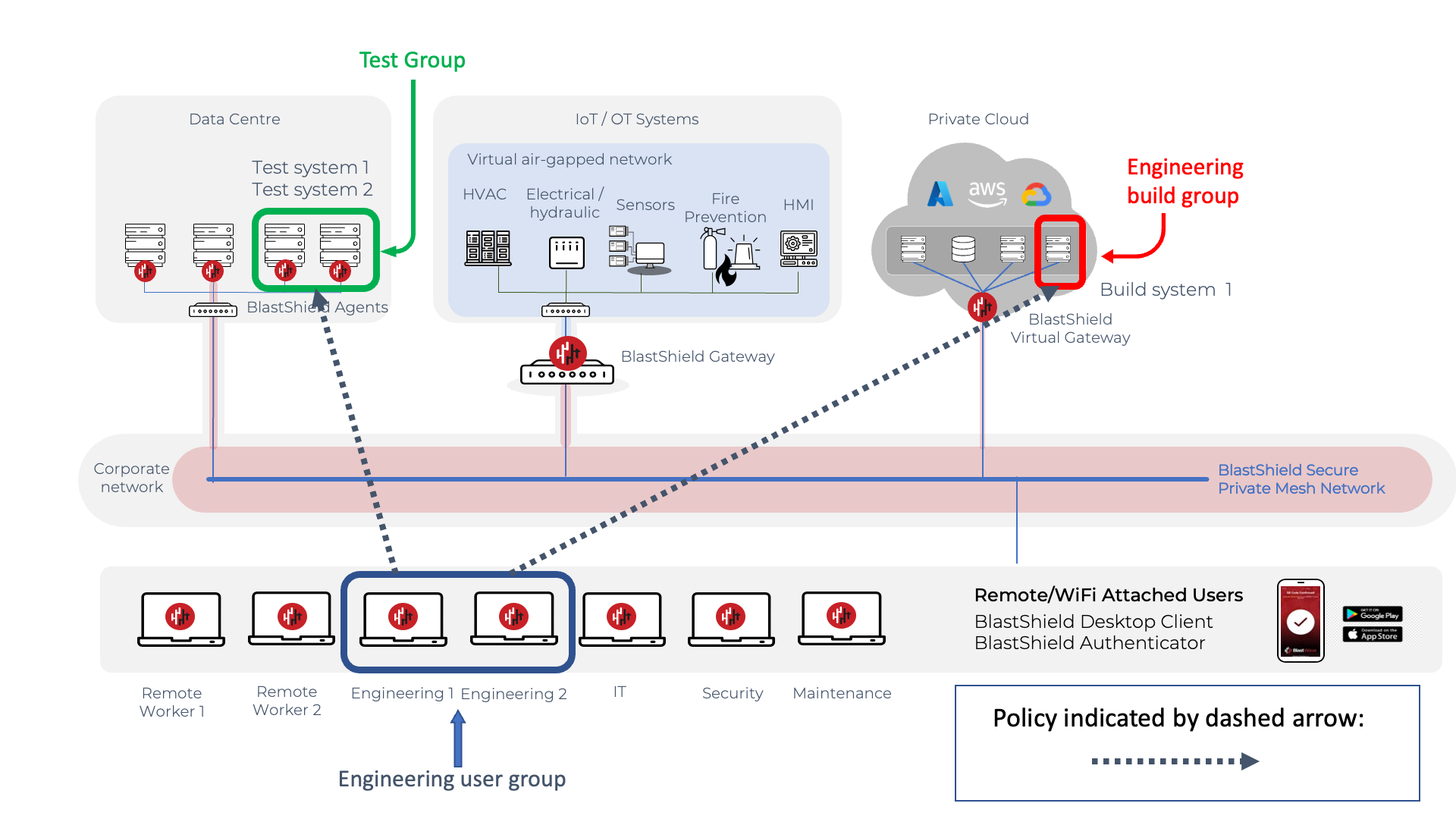
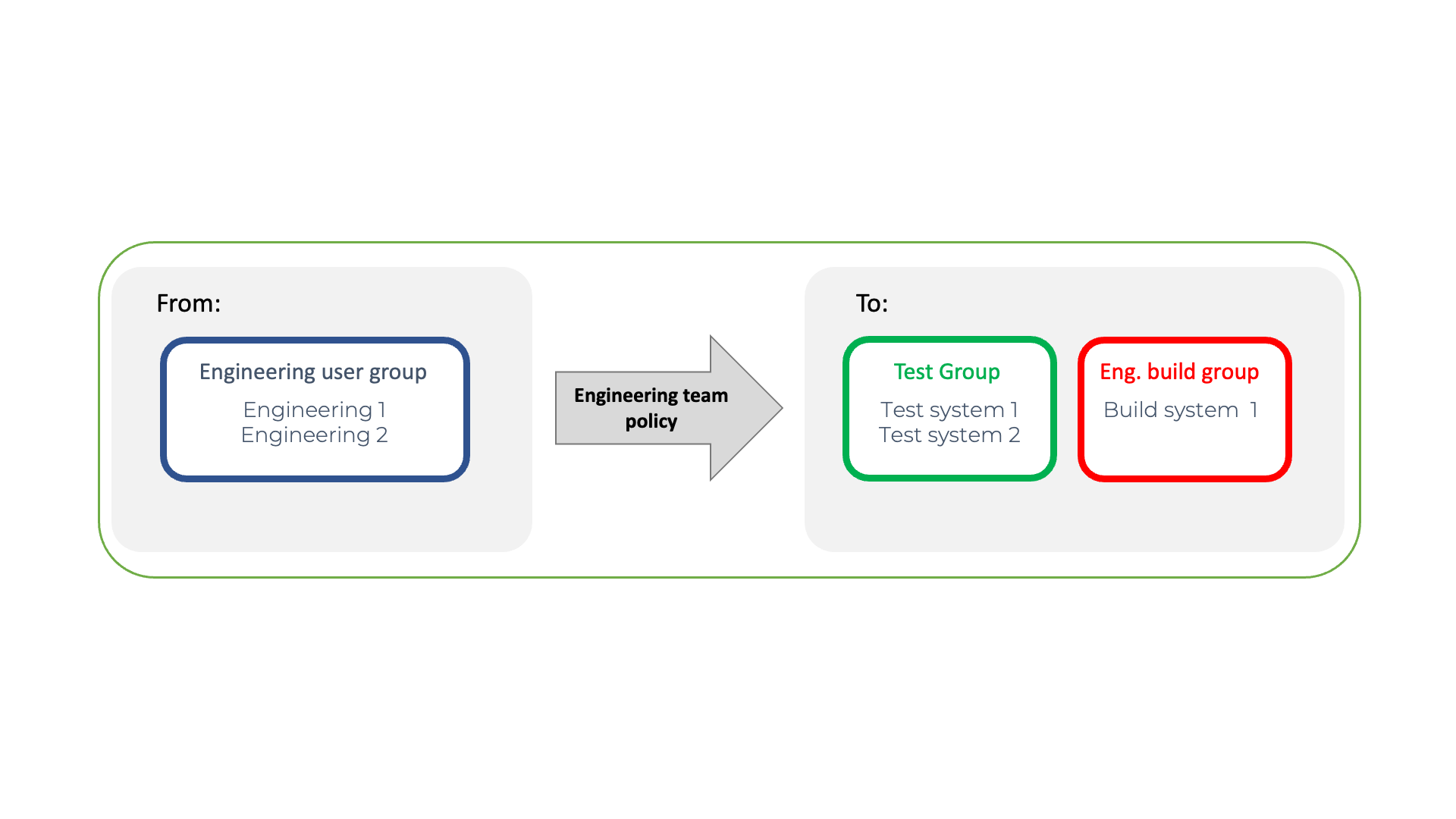
A policy example is shown below. The two test hosts are defined in a single group and the build host is defined in a separate group. This provides the isolation of these systems from all the other systems using micro-segmentation. The engineering user group is configured in a policy to provide micro-segmented remote access to the build and test systems and no other systems.
Example 3 Micro-segmentation of machine-to-machine monitoring
In this example, micro-segmentation is used to isolate an IoT sensor system and facilitate outbound access from this system to an external monitoring application. The IoT sensor system is virtually air-gapped by a BlastShield Gateway to provide a secure isolated environment for the OT and IoT devices. The monitoring platform is in a private cloud environment and is protected by a BlastShield™ virtual Gateway. This is an example of micro-segmentation within a machine-to-machine environment. Only the sensor system can communicate out from the secure environment to the monitoring system.
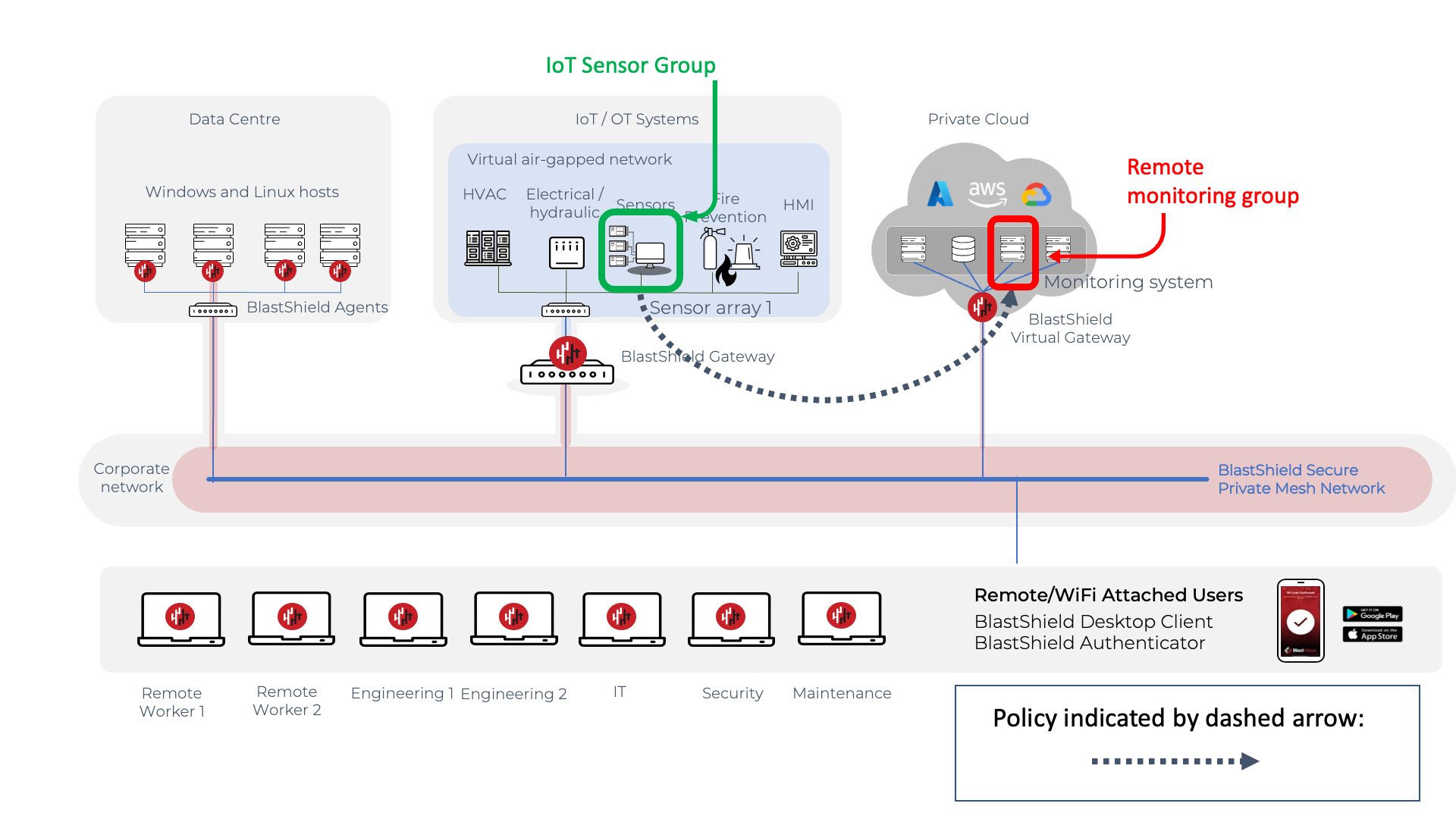
The policy for this is shown below. The the IoT Sensor device and the external monitoring host are both defined in groups. This provides the segmentation of the IoT device and the monitoring platform from all the other systems. The policy is configured to allow the IoT sensor group to open connections to the monitoring platform and no other systems. Due to the enforced micro-segmentation, no other IoT/OT device is allowed to use the policy.
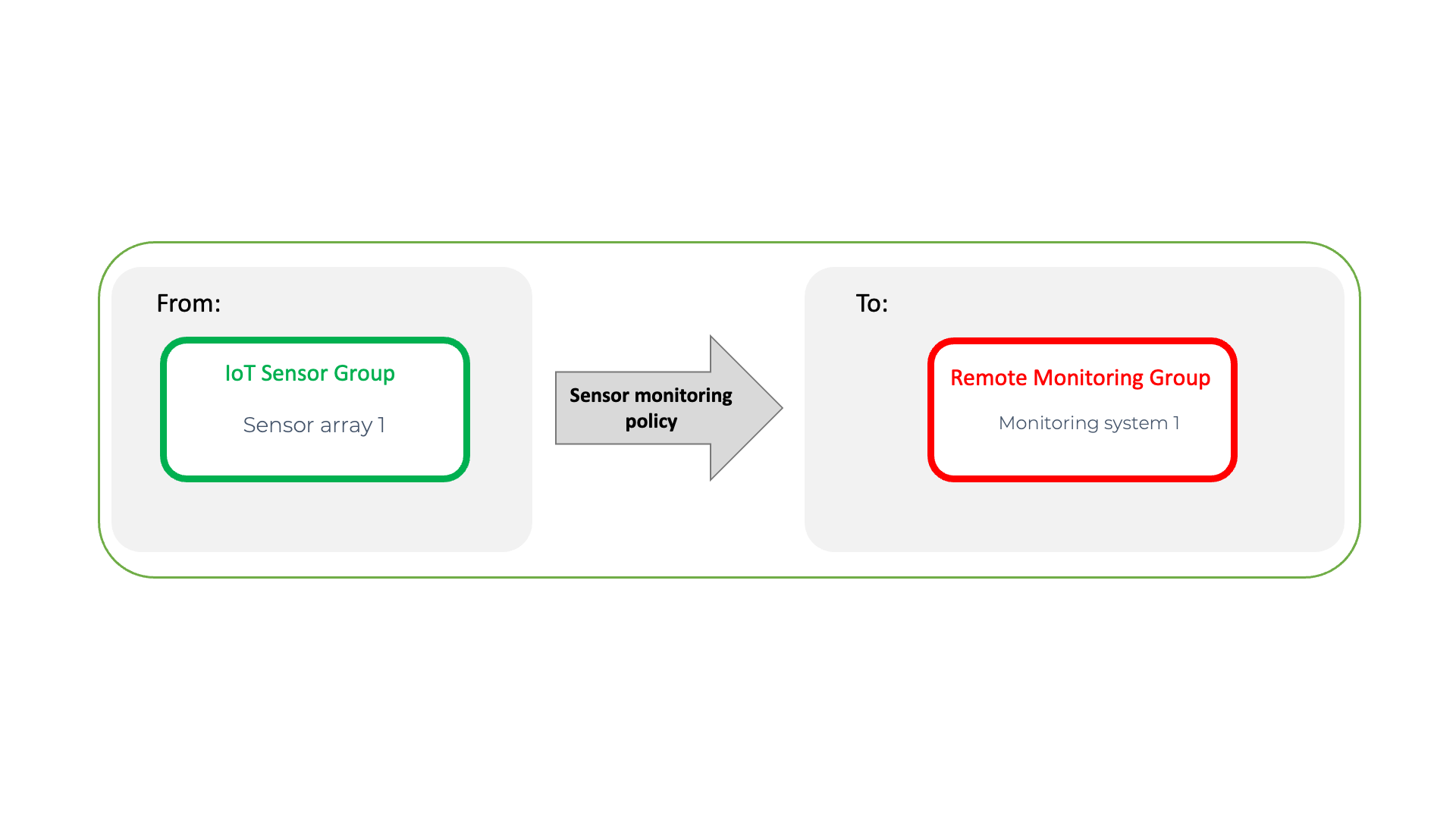
Configuration of micro-segmentation with zero-trust policy
The polices are simply provisioned in the Orchestrator exactly as shown above, using the graphical user interface. The figure below shows what the configured policies look like in the Orchestrator.
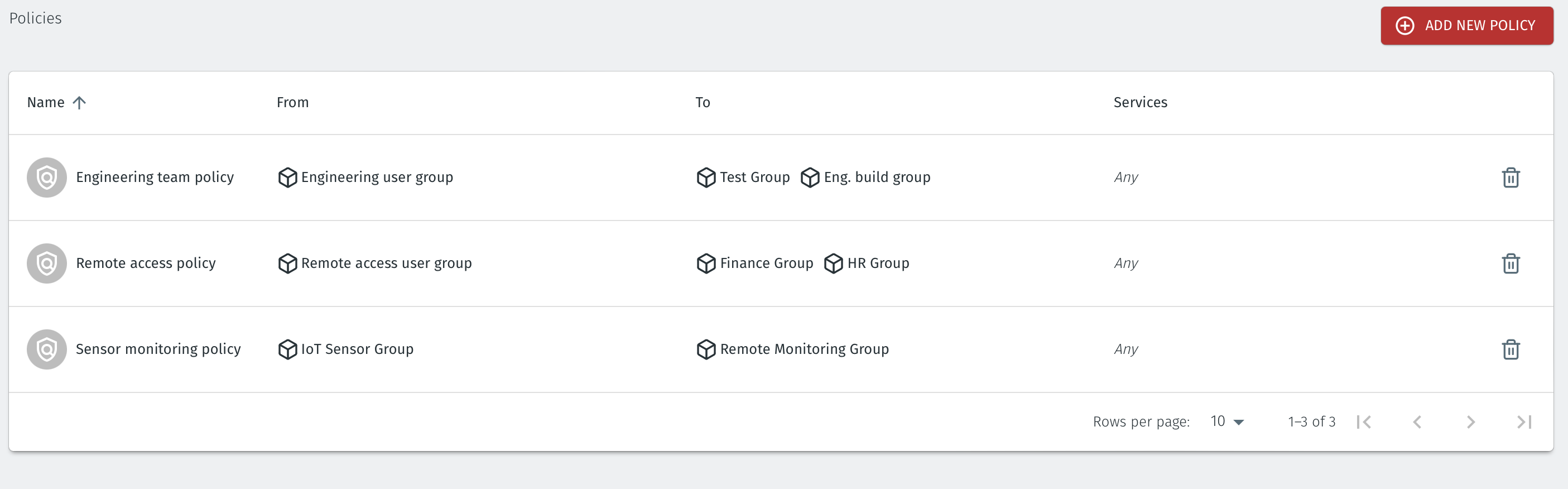
You can find out more about configuring groups and policies here: Groups Policies and Egress Policies