Gateway types and their use cases
The BlastWave Gateway may be deployed in different configurations depending on the required functionality and endpoint isolation requirements.
Three different deployment options are explained below. These are the passive mode NAT Gateway, an inline Gateway as a router replacement, and an inline Gateway using MAC or VLAN addressing modes.
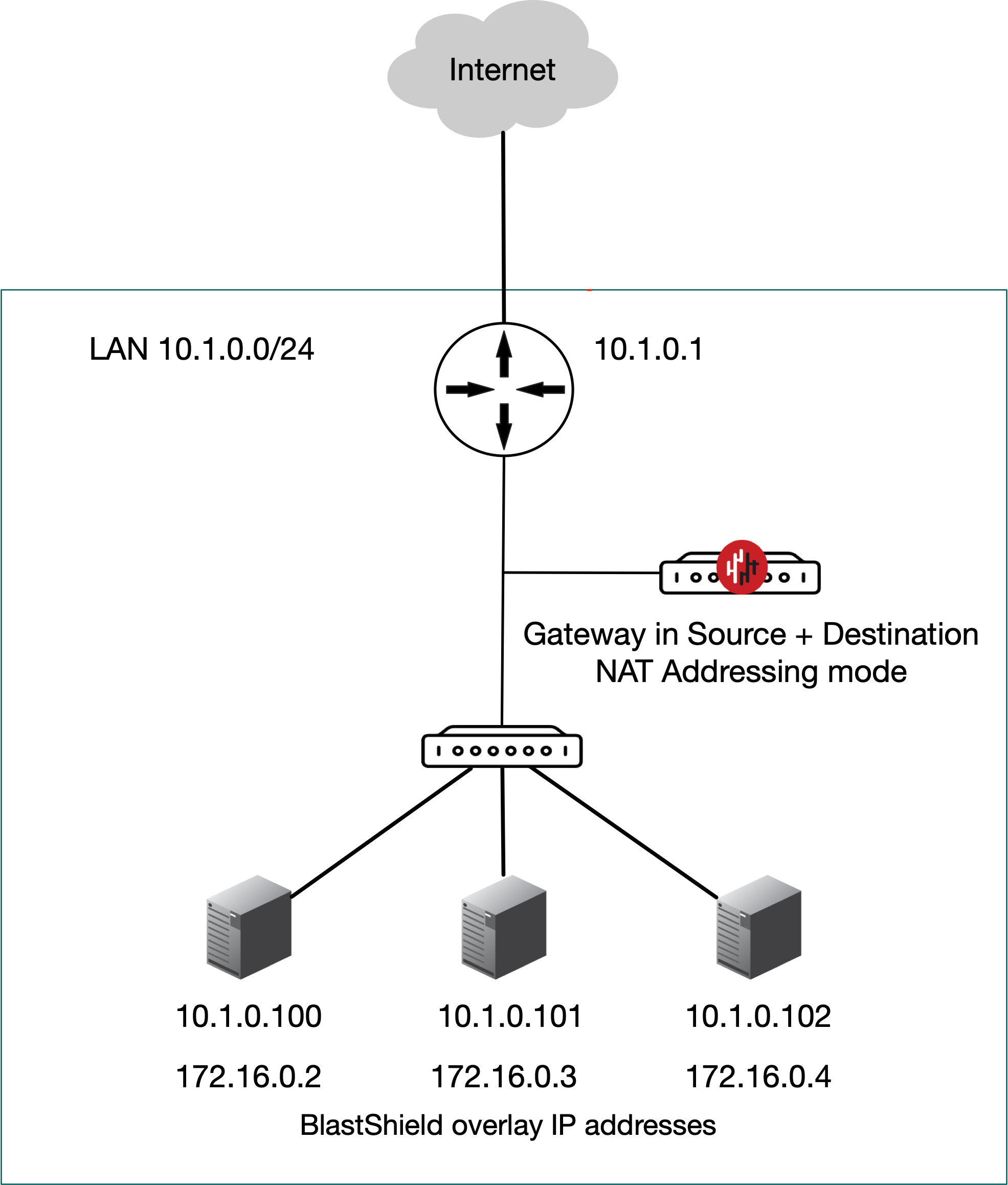
Passive Gateway (Source + Destination NAT addressing mode)
The Gateway is deployed passively to provide secure remote access to endpoints. It is installed out of line of the network path, so that it has no impact on the traffic between endpoints on the local network and requires no changes to the endpoints. No routing changes are required. All connections are encrypted end-to-end and micro-segmentation of users and endpoints with zero-trust policy is supported. The endpoints are able to communicate freely on their local LAN whilst at the same time secure remote access for users over the BlastShield™ network to these endpoints is managed by the Gateway. Endpoints will not be able to initiate connections out over the BlastShield™ network overlay because there is no route to the overlay network (if this is required, then use 'Destination NAT' mode).
A passive Gateway is configured by setting the Gateway addressing mode to IP Address (Source+Destination NAT). and it can be installed on hardware with a single NIC.
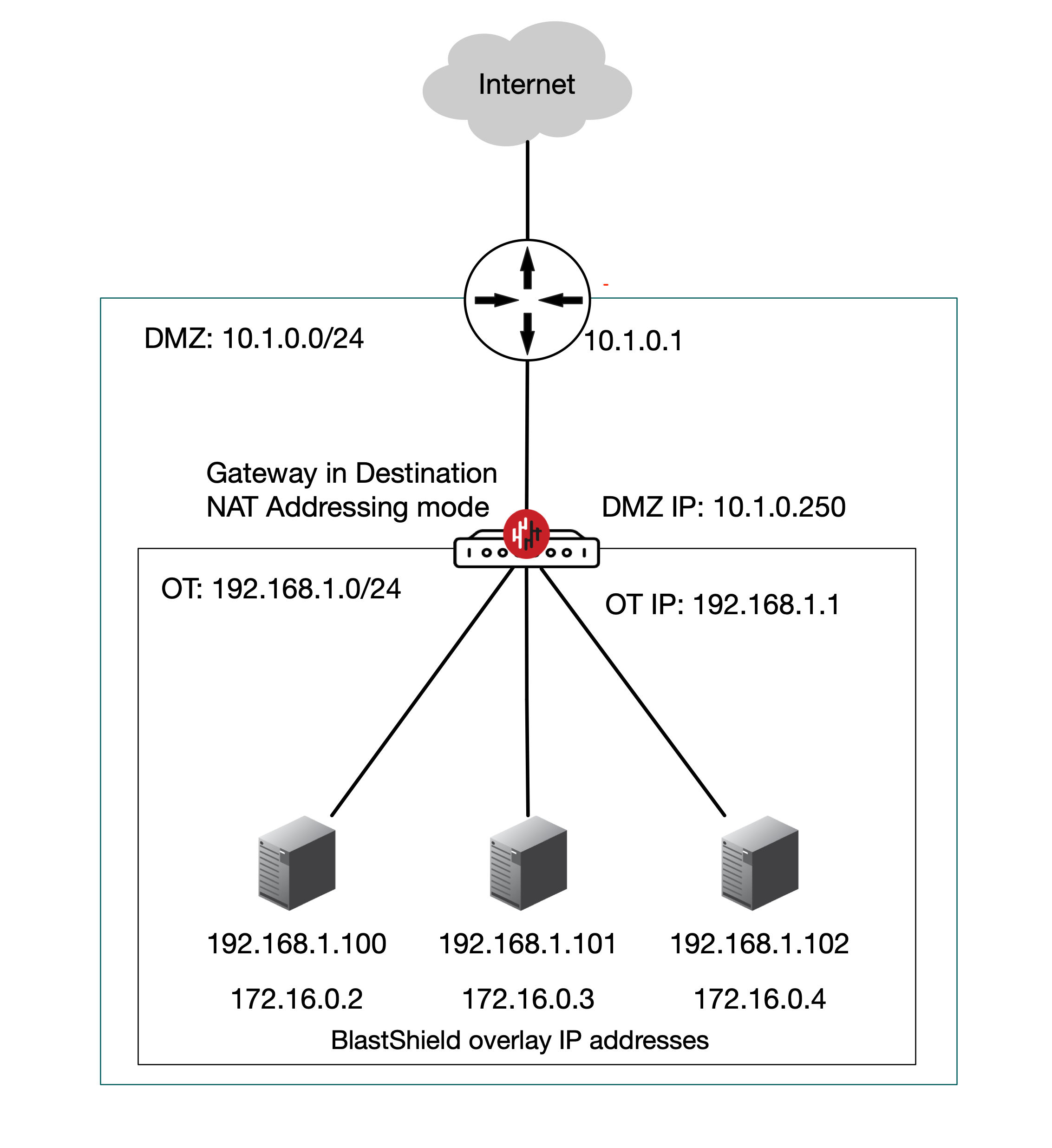
Inline Gateway as a router replacement (Destination NAT addressing mode)
In this scenario the BlastShield™ Gateway replaces the router between the OT and DMZ networks and performs all the routing between the subnets as well as providing secure remote access with microsegmentation of users and endpoints. The Gateway is located inline in the network path and provides isolation at the network layer, providing a virtual-air gap to protected endpoints so they appear invisible and isolated to unauthorized users. The endpoints are able to communicate freely on their local LAN if required or if strict local segmentation is required, this can be achieved by using an ethernet switch in port isolation mode or a Gateway appliance with multiple downstream ports.
Requires a routing change: endpoints will be able to initiate connections out over the BlastShield™ network, provided the endpoints have a route added to the BlastShield™ overlay via the Gateway local LAN address.
An Active Gateway as a router replacement is configured by setting the Gateway addressing mode to IP Address (Destination NAT) and it can be installed on hardware with two or more NICs.
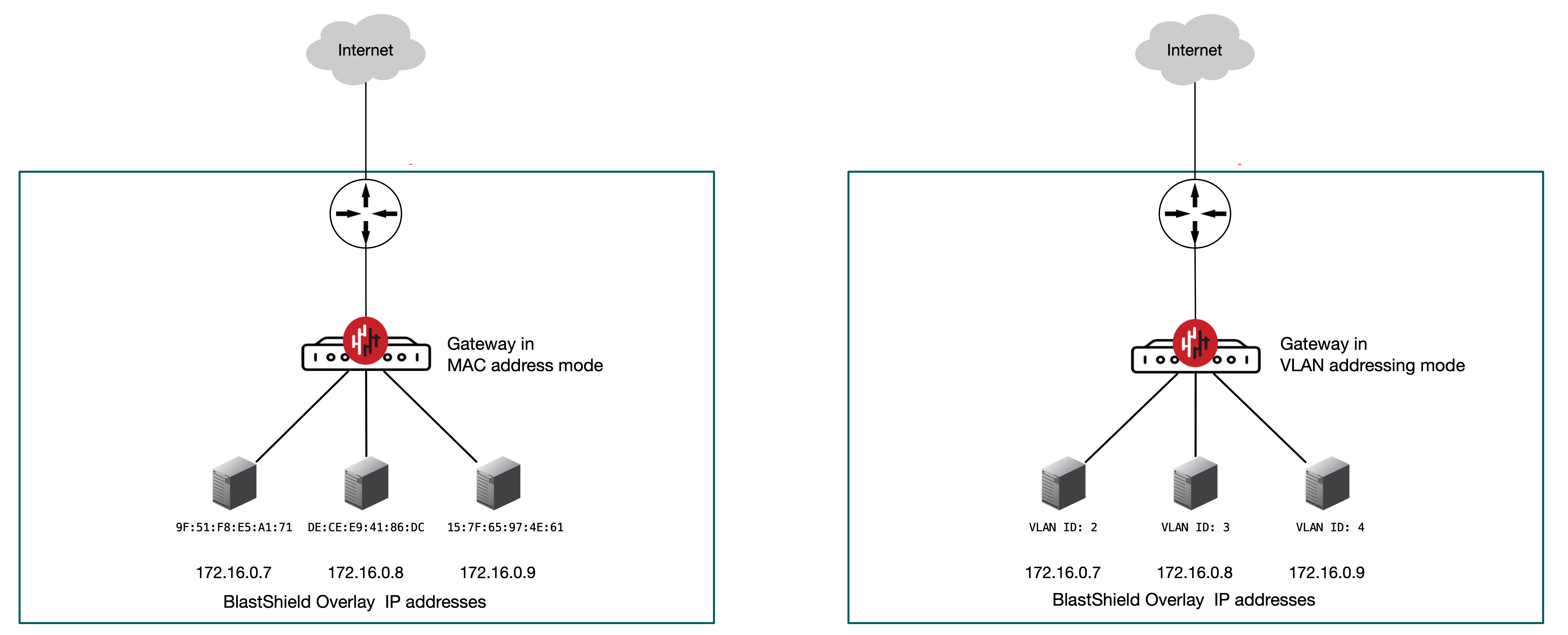
Inline Gateway using MAC or VLAN addressing modes
In this scenario, the Gateway is located inline in the network path as shown in the diagrams and the endpoints are allocated new IP addresses in the BlastShield™ overlay network by the Gateway.
All protected Endpoints downstream from an Active Gateway will be rendered invisible to the network underlay, and access control will be managed by BlastShield™ policy. The Gateway provides isolation at the network layer, providing a virtual-air gap and inhibiting unauthorized lateral movement between the protected endpoints, so that endpoints are not able to communicate freely on their local LAN unless authorized by policy. Endpoints will be able to initiate connections out over the BlastShield™ network to other authorized BlastShield™ nodes, but they will be unable to communicate with non-BlastShield nodes.
The Gateway is configured by setting the Gateway addressing mode either to MAC or VLAN and it can be installed on hardware with two or more NICs. You can optionally use a managed Ethernet switch downstream of the Gateway to allow multiple endpoints to be connected. If the Gateway is using MAC addressing mode, the Ethernet switch must be configured to work in port isolation mode, so that all downstream packets are forwarded to the Gateway. If the Gateway is using VLAN addressing mode, the Ethernet switch must be configured to assign a unique VLAN ID to each connected endpoint.