On-premise installation of the Orchestrator onto a bare-metal x86 appliance in a fully air-gapped network.
Introduction
The BlastShield™ Orchestrator is used to provision and manage all systems in a BlastShield™ network. This includes management of gateways, endpoints, remote users, groups, and policies. This article describes how to install a new Orchestrator into a fully air-gapped network. Once installed, you will use the Orchestrator to manage and provision all systems within the BlastShield™ Network.
Fully air-gapped deployment
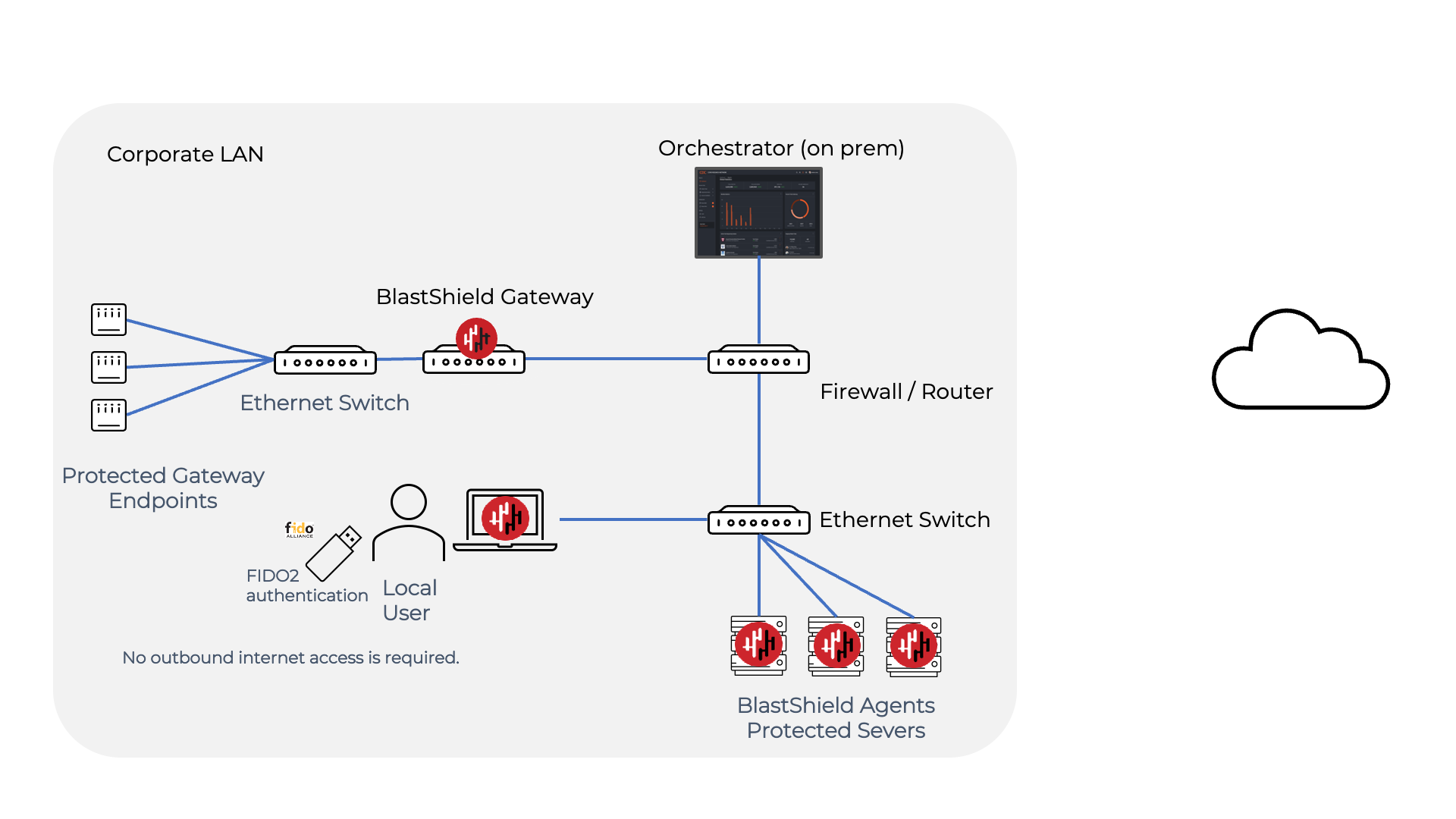
Local regulations may sometimes require a fully air-gapped deployment, where no external access from the network is permitted. In a fully air-gapped network the Orchestrator is deployed on premises with no access to the internet, and similarly, users are also not allowed external internet access.
Deployment notes for a fully air-gapped deployment
Because the BlastShield™ Mobile Authenticator app requires external access it may not be used in a fully air-gapped network and FIDO 2 keys must be used for user authentication instead.
You must manually process the Orchestrator license request during the installation. This is a one-time process.
Any Gateways or Clients (eg user workstation running the BlastShield™ Client) must have it's DNS set to the IP address of the Orchestrator.
As the Orchestrator will be self-hosted, you should provide your own certificate for the Orchestrator HTTPS web UI.
Request the Orchestrator BSI invitation file and the administrator BSI invitation file from BlastWave. This are used for registering the BlastShield network and for registering the administrator user.
The Orchestrator will use UDP port 12345 for communications. Please forward UDP Port 12345 inbound on the firewall to the Orchestrator.
Install a BlastShield Client on the administrator workstation. You can download the Client from here.
Download the Orchestrator firmware. You can download the Orchestrator firmware here.
Make sure you have a suitable hardware platform on which to install the Orchestrator.
x86 Orchestrator hardware requirements
Parameter | Value |
|---|---|
CPU | Minimum Intel Atom with AES-NI support or Intel Celeron with AES-NI support. Note that more powerful CPUs with AES-NI support such as Core i3 or Xeon are also supported. |
RAM | Minimum 8GB |
HDD/SSD | Minimum 64GB |
NICs | One NIC is required. Most NICs made by Intel, Broadcom and Mellanox are supported. |
Note: a USB interface is required to connect the boot media.
In this step you will be downloading the BlastShield™ Orchestrator Software Installer. Using the Invitation (.bsi) file you received from BlastWave, you will prepare a USB installer to install the software on your x86 platform and bind it to the BlastShield™ Network. Below are the steps to prepare the installation media.
Download the firmware if you have not already done. You can download the Orchestrator firmware here
Unzip the Installer Package (Do NOT run the Installer file).
Write the Installer image to a USB drive using any available image writer
Note: there are several free utilities available for writing images to USB drives. We recommend the balenaEtcher software, but you can use any utility.
Once you have written the image to the USB, copy the Orchestrator BSI invitation file into the root folder of this image on the USB.
Create a file and name it
authorized_keysThis file should contain a SSH public key in one-line OpenSSH format which will be used by the administrator to apply the license to the Orchestrator immediately after installation.
Add the SSH public key to the
authorized_keysfile and copy this file to the root folder of the USB.
Note
The USB should contain the following:
The installer image.
The BSI file.
The
authorized_keysfile.
In this step you will be booting the x86 platform from the USB image created in the previous step.
Connect your x86 platform as shown here and then follow the steps below.
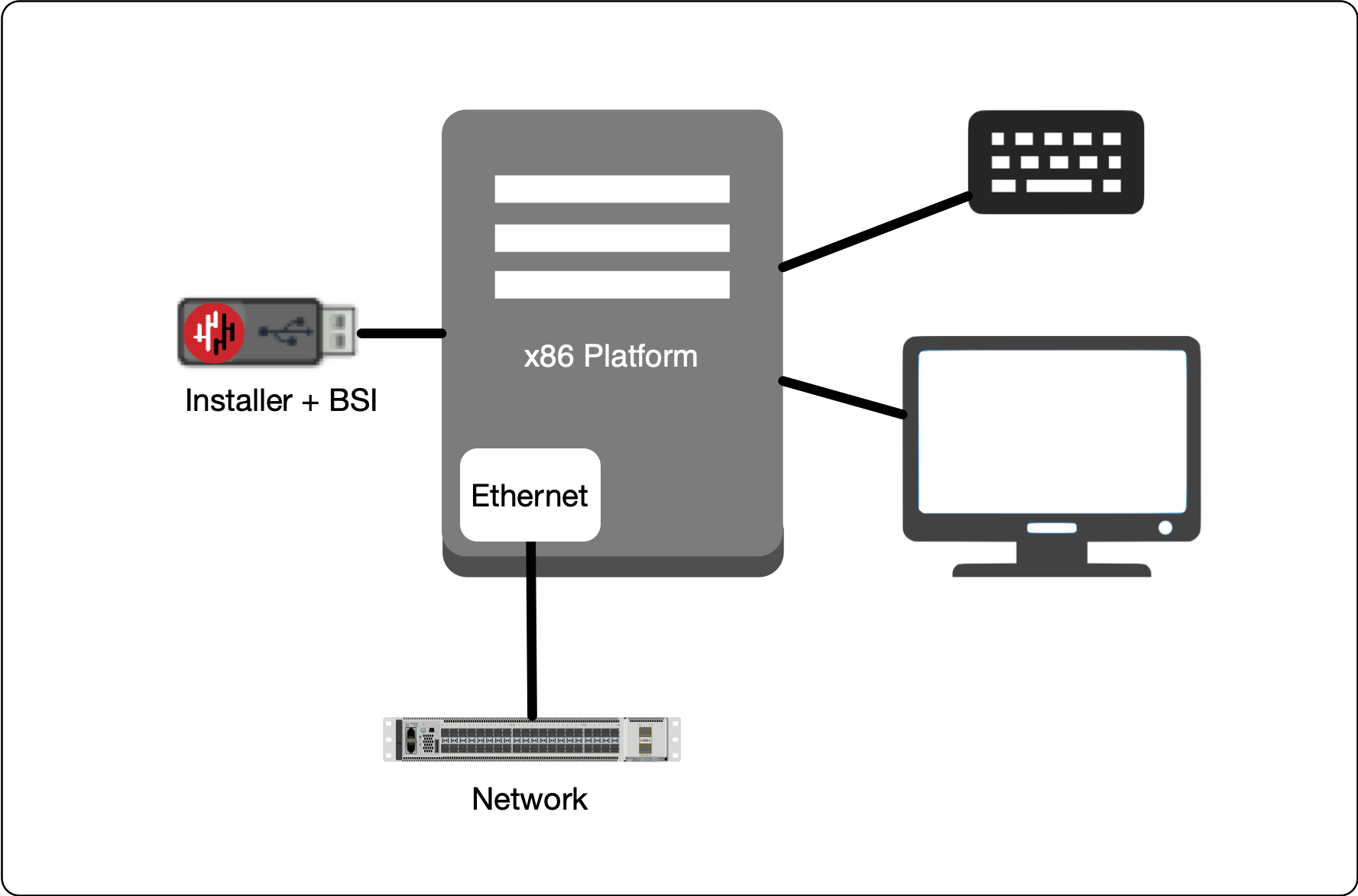 |
Making sure the x86 server is connected as shown above, power it on and exit the boot sequence using the break key that applies to your hardware, then select the boot setup menu. Ensure the USB boot media is connected.
Re-boot your server from the USB image, once the image boots you will begin the setup process.
Select the uplink (network) interface for the Gateway from the displayed list (note that the Orchestrator will not use any endpoint interfaces).
Set the IP address, Default Gateway and DNS server IP address. Please note that for an airgapped Orchestrator, the DNS IP address must be configured to the same address as the Orchestrator IP address (for a non-airgapped Orchestrator deployment you should provision the DNS to your network's preferred DNS server, please refer to the non-airgapped x86 installation for more details).
Wait for the network interface to come up.
Select the invitation (.bsi) file.
Select the target device (hard drive).
Confirm that all data will be erased and the image will be installed on the server.
When the installation is complete you will be prompted to remove the USB media. at this point, and the server will re-boot.
Remove the USB.
Click on OK
The VM will gracefully restart.
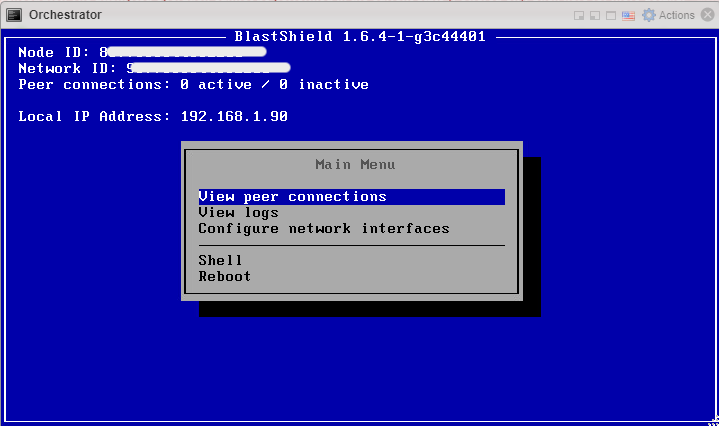
Once the Orchestrator has started, you will see the local maintenance interface displayed on the console. The local IP address of the Orchestrator is displayed. You will use this address to SSH to the Orchestrator in the next step.
Forward UDP Port 12345 inbound on the firewall to the Orchestrator.
SSH as admin into the new Orchestrator. Authentication is done by your SSH public key which was added during the VM setup.
Copy the content of
license_req.jsonwhich is generated in the home directory of the admin user.$ cat license_req.jsonReturn this content to BlastWave. BlastWave will reply with a license key.
Whilst still connected to the Orchestrator by SSH, run the
apply-licensecommand and hit enter.$ apply-licenseYou will see the following prompt:
License:At this prompt, paste the license key information to the command line and hit enter to start the Orchestrator.
License:{"license": "..."}
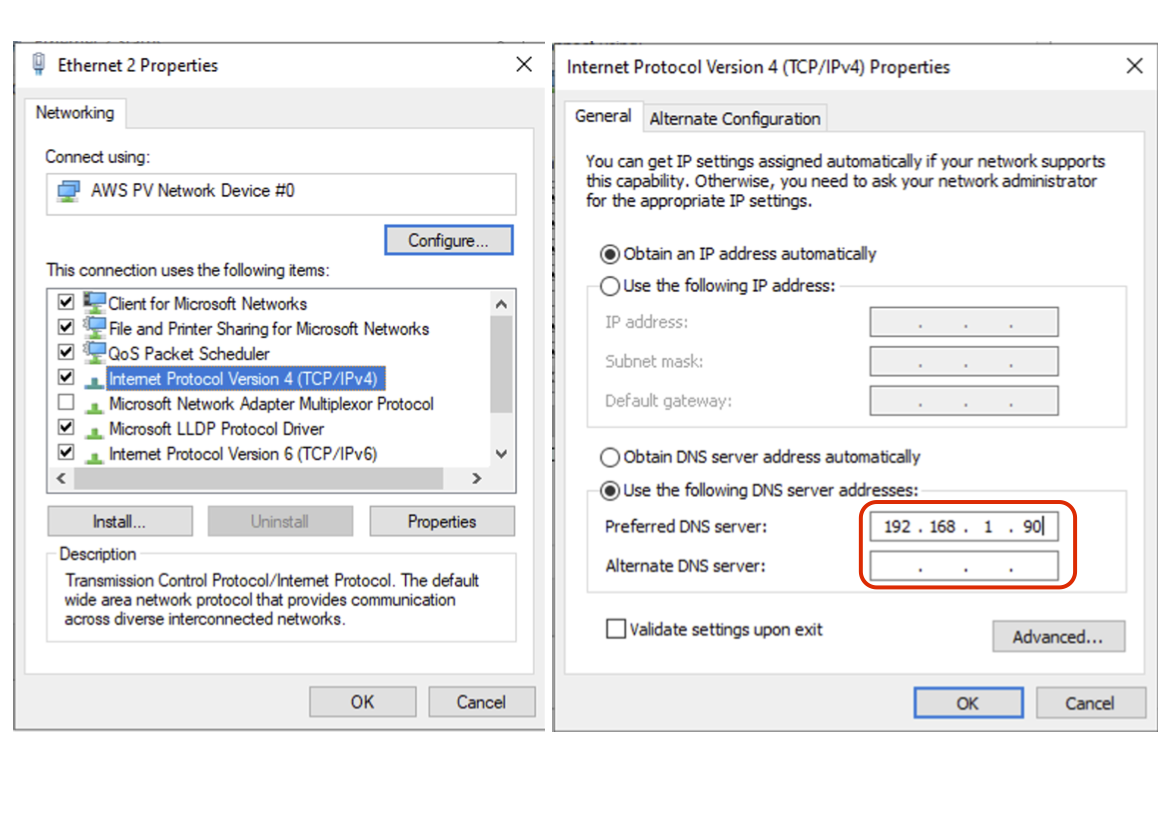
Any device running the BlastShield™ Client must have it's DNS set to the IP address of the Orchestrator.
In a Windows desktop OS, you can change the DNS settings in the network interface properties > TCP/IPV4 settings.
On macOS the DNS can be changed in the network System Settings
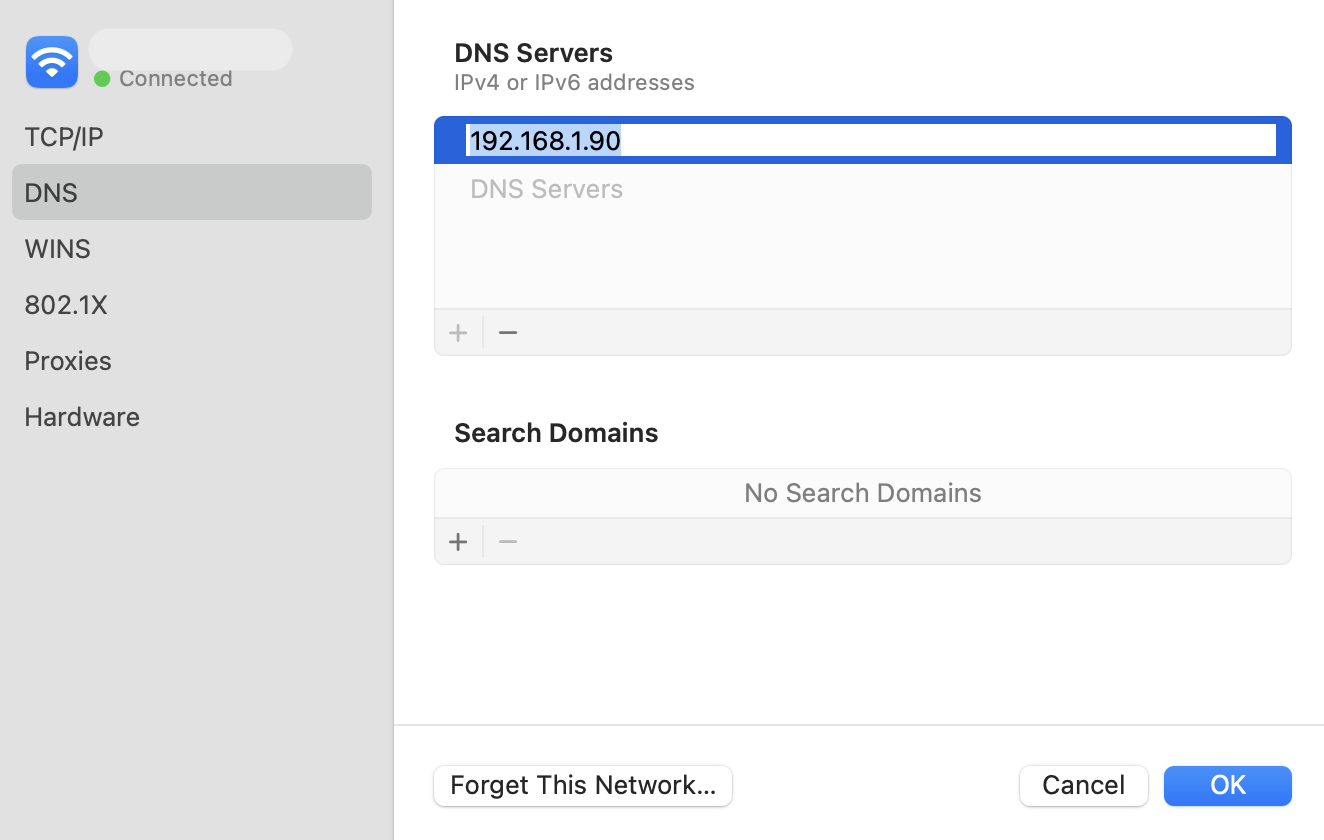
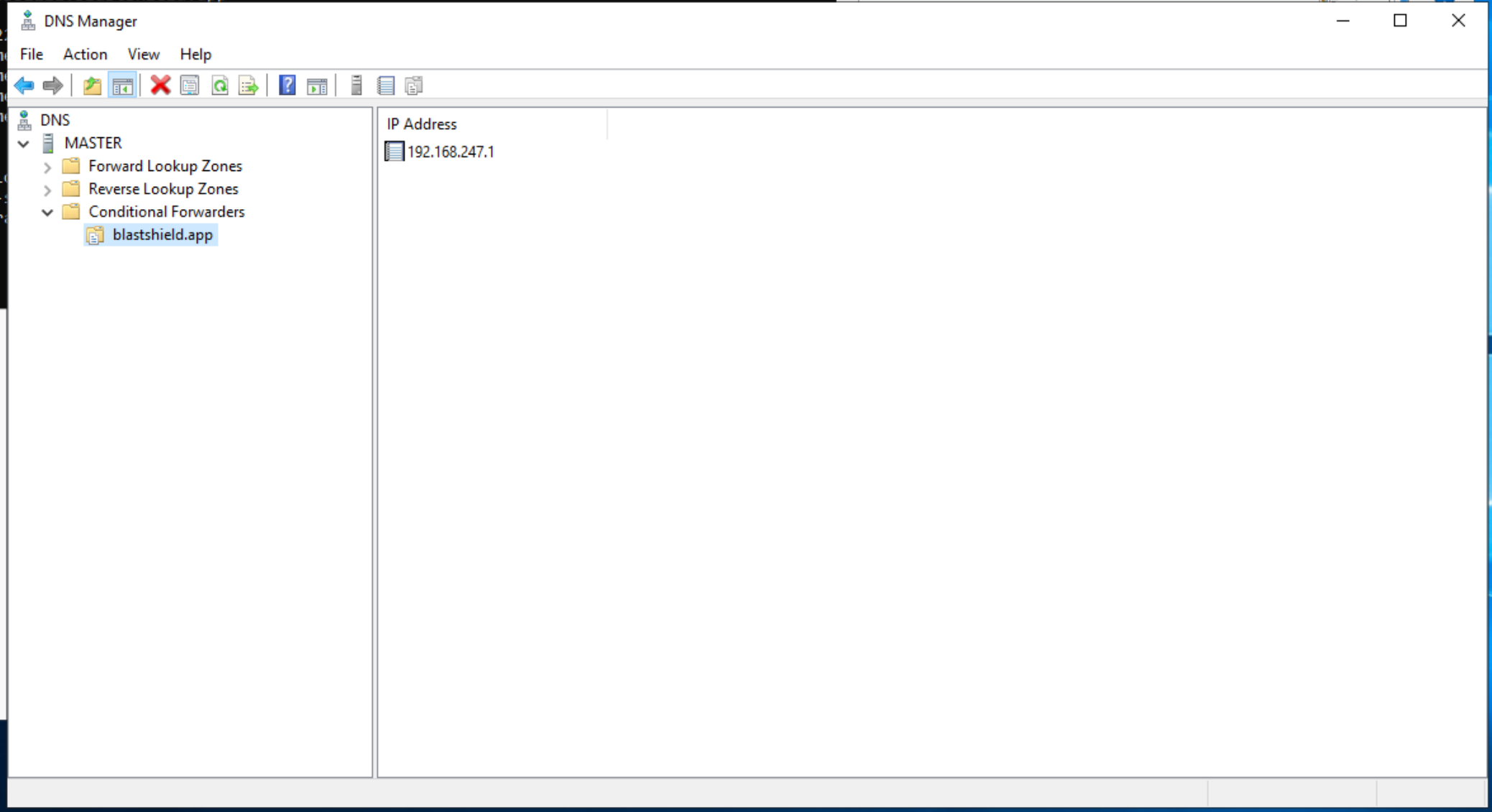
For networks which use an on-premise Microsoft DNS or an AD server for DNS, then a conditional forwarder can be added with the Orchestrator IP address as shown for the domain
blastshield.app. In the example images below, 192.168.247.1 is the IP of the Orchestrator.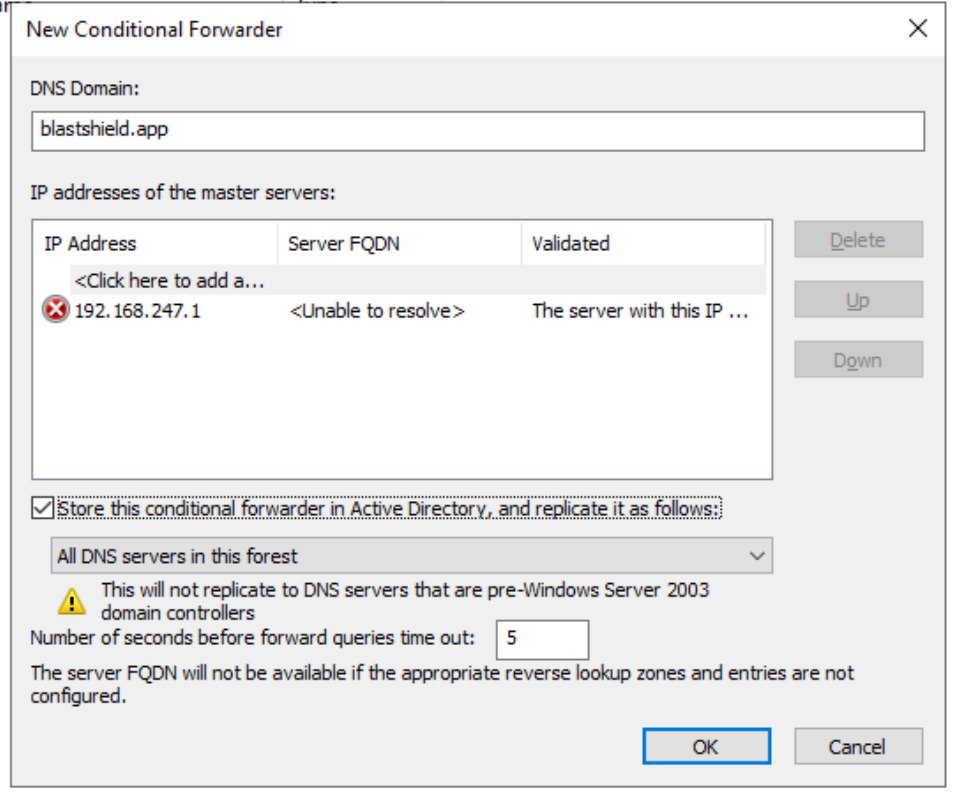
Here you will use the administrator BSI invitation file which you received from BlastWave to register and connect to the Orchestrator as the administrator user.
Ensure your registered FIDO 2 Key is plugged into your computer.
Launch the BlastShield™ Client App and click on FIDO2 Key.
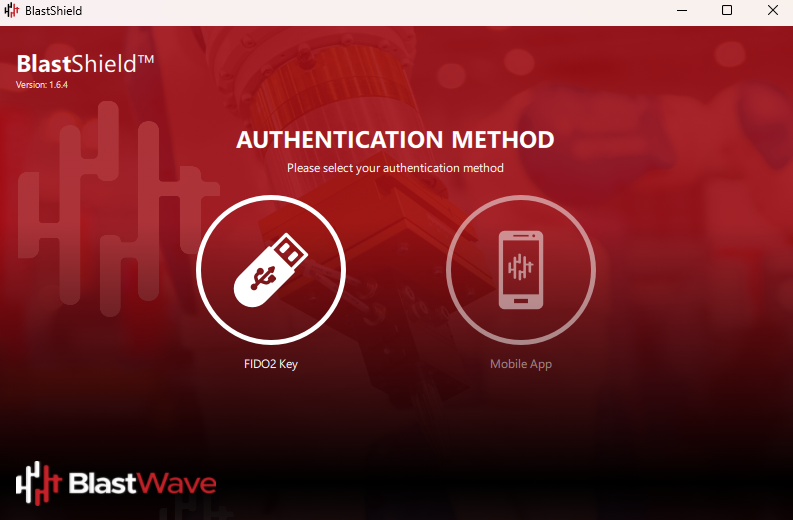
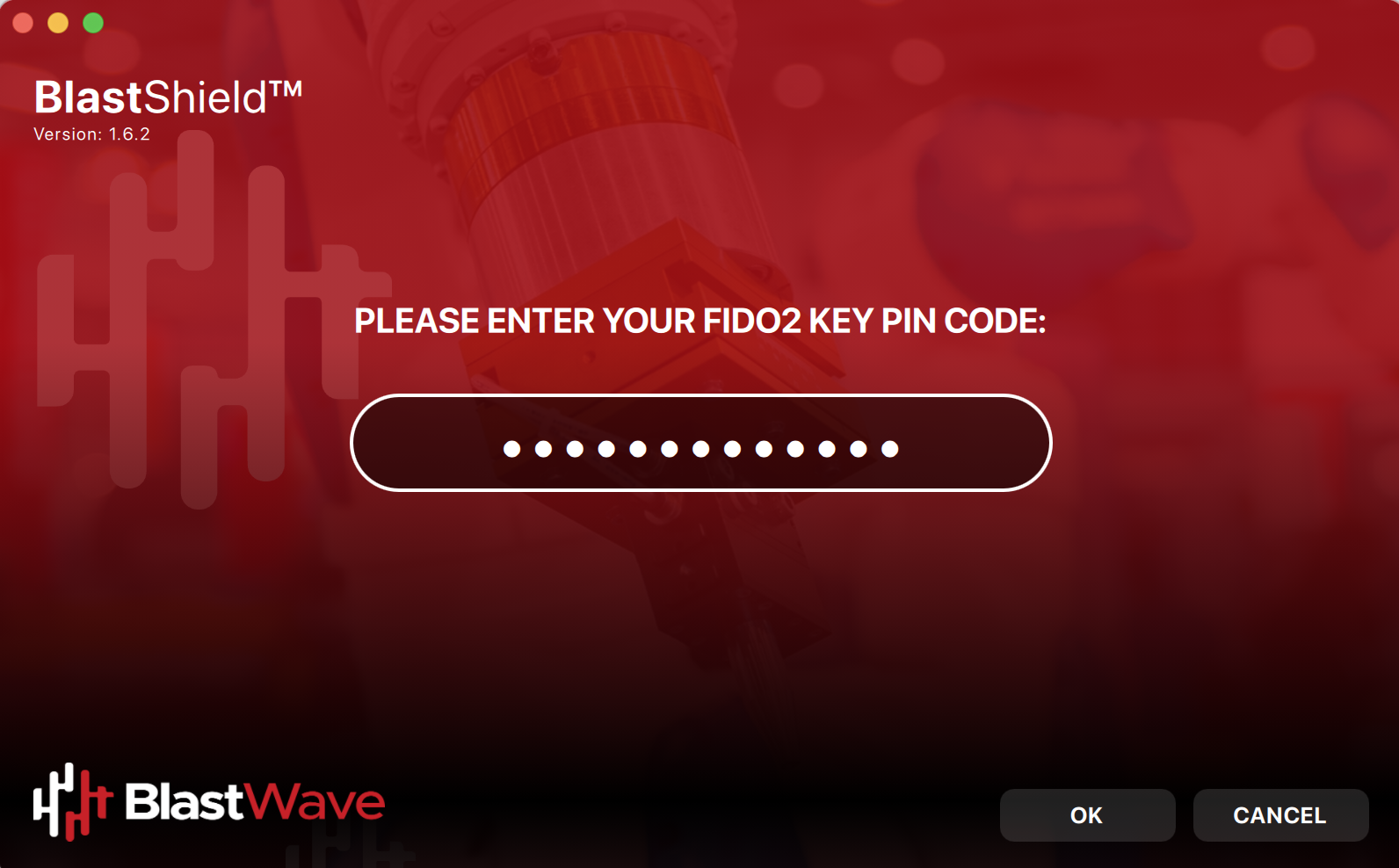
Enter the security PIN for your FIDO 2 Key.
Select Add new - this is when you will register this key to the network.
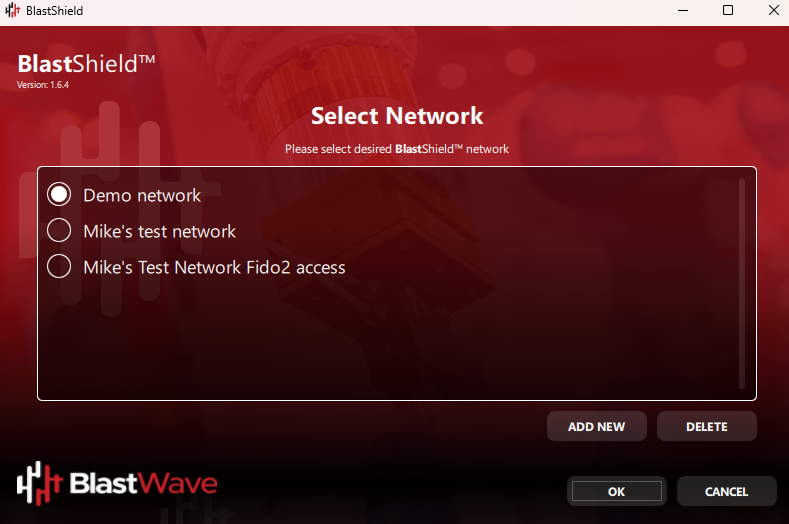
Locate and select the administrator invitation file (.bsi) for this key.
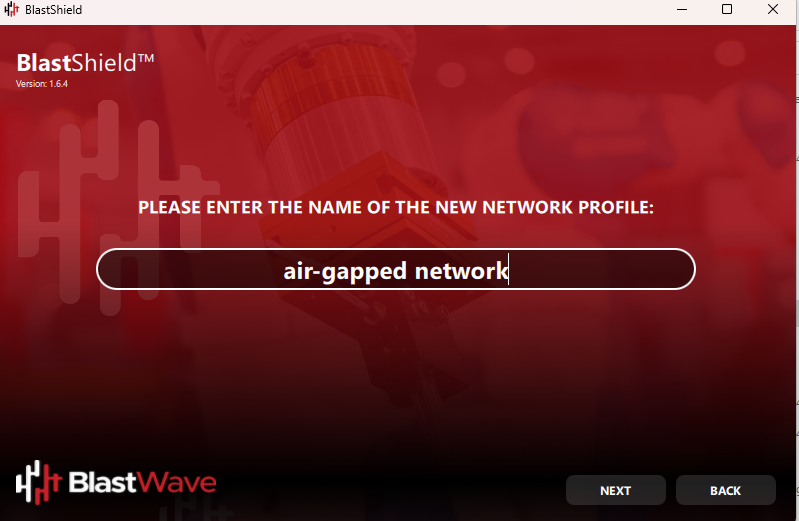
Enter a name for this network (Note: this can be any name of your choosing).
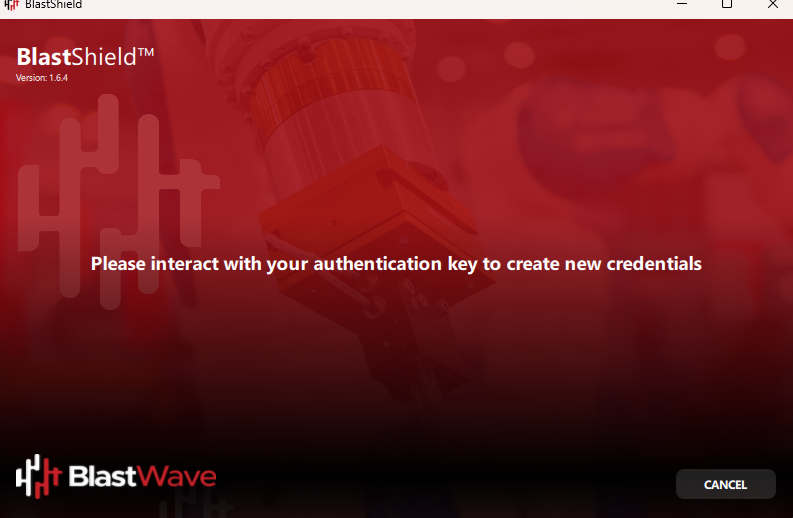
You will be prompted to touch both metal sides of your FIDO 2 key to create new credentials.
Next, you will be prompted to touch the key again to sign in to the network.
At this point you have registered your FIDO2 key to the network, and are signed in to the BlastShield™ network.
On the BlastShield™ Client, click on the Launch Orchestrator button.

Interact with your FIDO2 key when prompted.
The Orchestrator administration UI will open in your default web browser. At this stage the UI web server will be using a self-signed certificate for HTTPS, so you should acknowledge the browser security warning.
Now that you have installed and connected to the Orchestrator, you can add Host Agents, Gateways and new users. Please refer to the following sections to learn how to do this.