BlastShield™ Overview and Architecture
BlastShield™ is an encrypted peer-to-peer software defined perimeter overlay network that creates a zero trust protective shield around critical IT/OT assets and data by making them undetectable by modern network scanning and traffic analysis tools.
BlastShield™ simplifies network security by combining several functions into a single product, namely:
Phishing-resistant passwordless multi factor authentication (MFA).
High performance, peer-to-peer software defined perimeter.
Zero trust, policy based access.
Encryption of data in motion
Micro-segmentation and invisibility of protected assets at the network layer.
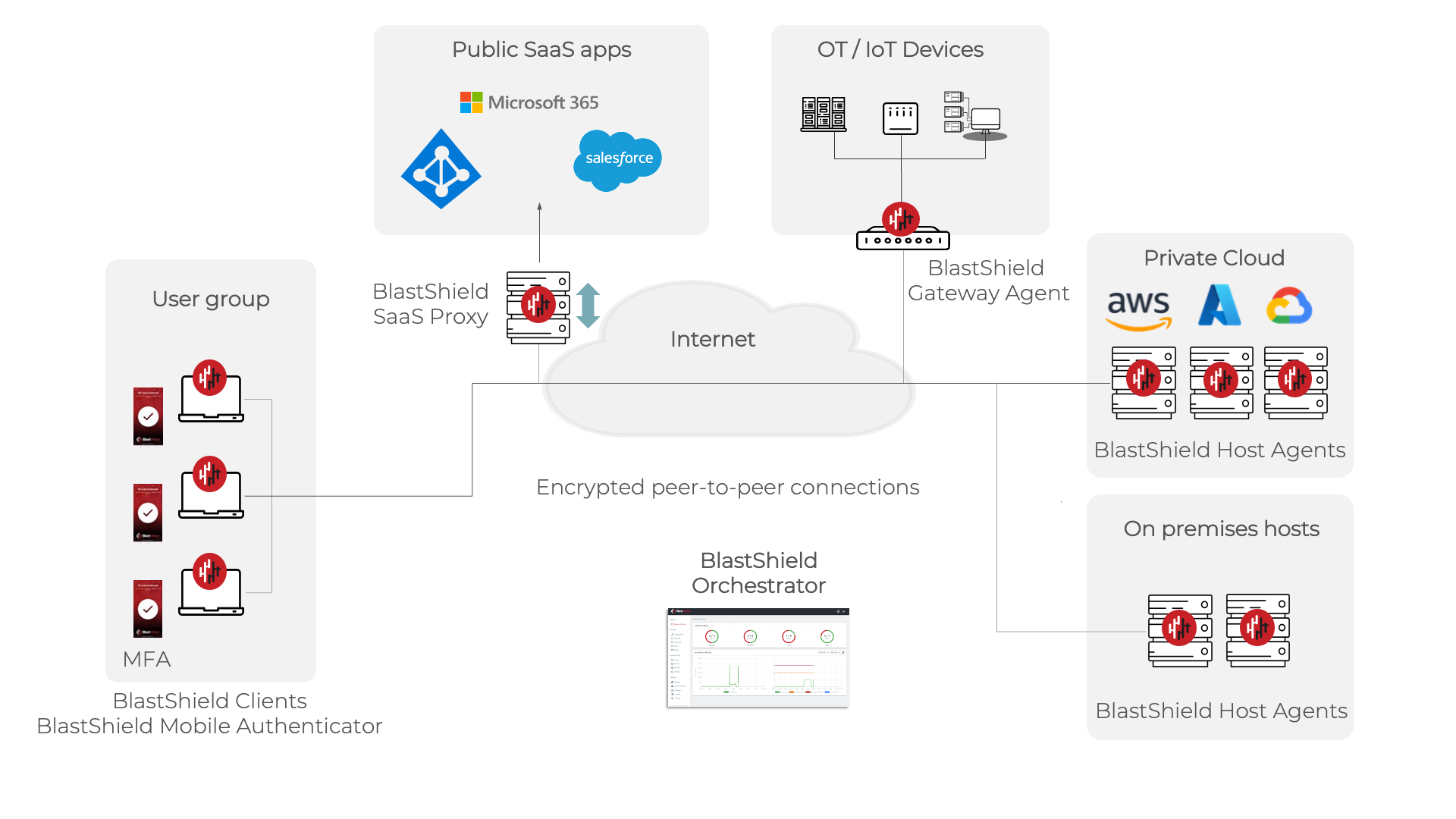
BlastShield™ is deployed as an in-line IP sub-network within an open IP network that creates a zero-trust protective shield around critical infrastructure assets and data by rendering them undetectable by modern network scanning and traffic analysis tools. BlastShield™ provides a tunnelled secure network overlay for users and protected devices which is encrypted on a peer-to-peer basis and can only be accessed if a user or node has authenticated and is allowed by policy.
Architecture
A BlastShield network consists of multiple nodes, a node being either a User, Gateway or Agent where each of which is configured for secure, encrypted communication of data over a general network. The nodes and protected devices are organized as a mesh such that the protected devices are undetectable and un-addressable via the general network by entities external to the mesh. The BlastShield™ network is implemented in software as an encrypted peer-to-peer overlay on the existing network.
The BlastShield solution is illustrated below.
Compatibility
BlastShield™ runs over any network (TCP/IP, SCADA, Internet, SD-WAN, etc.). In fact, BlastShield™ can even run over raw ethernet. This flexibility makes BlastShield™ perfect for complex network environments.
Deployment
BlastShield™ is very easy to deploy, and a small network can be up and running in minutes. Each node will automatically discover the presence of the other nodes, determine data communication routes to the other nodes, and establish point-to-point encrypted tunnels between themselves and selected other nodes. If you want to learn how to deploy a BlastShield™ network you can view the Quick Start guide.
Access and authentication
A user can remotely access a BlastShield™ network using the BlastShield™ Authenticator app or a FIDO2 compliant Key. Both methods are highly secure and eliminate common threats such as phishing, and lateral attacks.
BlastShield™ uses passwordless multi-factor authentication (MFA). There is no username or password required. This makes BlastShield™ highly resistant to password theft, phishing and replay attacks because there is no password to lose or steal.
User identification in the BlastShield™ network is based on public-private keypairs. All network users identify themselves using a combination of a randomized 64-bit node identifier and a 256-bit elliptic curve keypair. A public-private keypair is generated when a new user registers with the BlastShield™ network.
Asset isolation and invisibility
A BlastShield™ Gateway (a software instance) that is in-line in front of the protected assets will isolate all those connected assets at the network layer. Any packets which cannot cryptographically authenticate with the Gateway will be dropped at the Gateway's external interface and only authorized and authenticated BlastShield™ users will be able to access the assets. Unauthorised connections will not be allowed and any network scanning tools will not be able to see the protected assets.
BlastShield™ will reject unauthorized connection attempts using the following methods:
TCP connections will be reset.
All other protocols will receive a ICMP ‘destination host unreachable’.
BlastShield™ Desktop Client.

Free downloadable software client available for Windows, MacOS, Linux, Apple iOS and Android.
The BlastShield™ Client provides secure user access to the BlastShield™ network. It is installed on a user device and is available for Windows, Linux, macOS, and also supports iOS and Android for use on tablets.
For the trial, the BlastShield™ Client will be installed on the trial user's computers.
BlastShield™ Mobile Authenticator app
Free downloadable software Multi Factor Authenticator App available from Play Store and App Store.
The Mobile Authenticator is an application for iOS and Android mobile devices for user passwordless MFA. It is available via the Apple App Store or Google Play Store.
For the trial, the BlastShield™ Authenticator will be installed on the trial user's mobile devices.
FIDO2 Key

Optional authentication key. Alternative to BlastShield™ Authenticator App.
A FIDO2 key is typically used in environments where mobile devices are not used.
BlastShield™ Orchestrator.
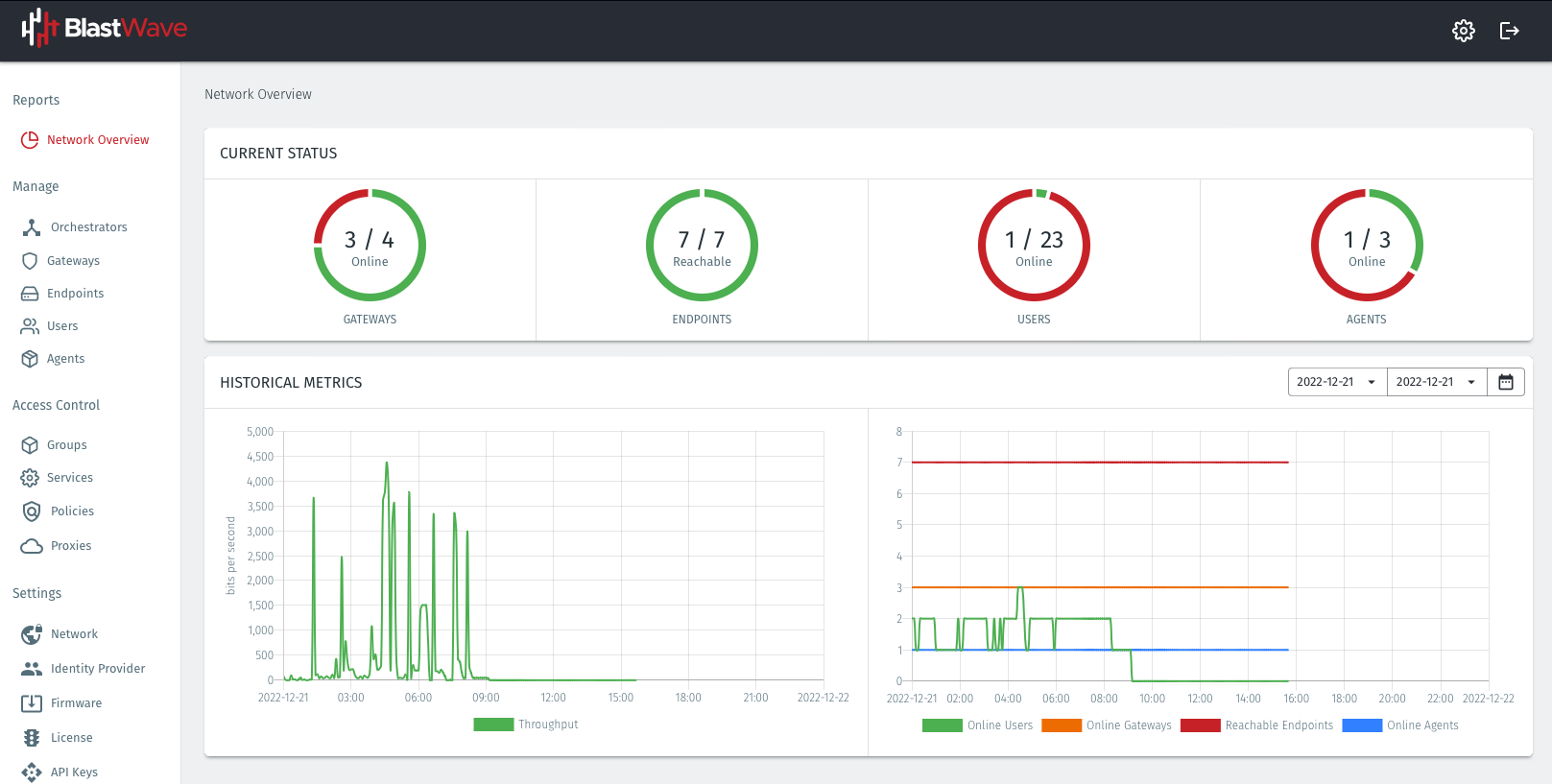
Cloud or On-Premises hosted Orchestration Application.
The Orchestrator is a server hosted by BlastWave that is used to create, modify, and remove all system users and policies within the BlastShield Network. Only users with authorized privileges can access and use the Orchestrator.
One Orchestrator will be deployed as a cloud instance for the trial.
BlastShield™ Gateway.
Downloadable software gateway that runs on most x86 platforms. Typically deployed in line to secure multiple assets that cannot host a BlastShield™ Host Agent or Virtual Gateway. Usually deployed in front of a network switch.
The BlastShield™ Gateway is an Agentless solution that is ideal for protecting OT and IIoT assets, or legacy computing assets that cannot support running an Agent.
A Gateway is deployed as a software image running on an x86 hardware of your own choice, or as a virtual machine.
BlastShield™ Virtual Gateway

Downloadable software gateway that runs in the Cloud (AWS, Azure, GCP) or on a hypervisor (VMware).
The Virtual Gateway is typically used to protect private cloud virtual instances, auto-scaling endpoints and serverless functions.
BlastShield™ Host Agent.
Downloadable software Host Agent that runs on modern Windows, Linux and macOS platforms. .
The BlastShield™ Agent is an application installed on your servers which enables secure peer-to-peer access from the BlastShield™ protected network.
A BlastShield™ Agent installed on a host will only allow access from authorized and authenticated BlastShield™ Users to its interface. Access to the Agent interface is controlled by policy using a zero-trust access methodology where particular users and assets must be authorized by policy before they can access the Agent.
The Host Agent can be deployed on on-premises hosts, on virtual machine instances or on private cloud virtual instances.
BlastShield™ SaaS Proxy
Downloadable software agent that runs on most modern Windows, Linux and macOS platforms.
The SaaS Proxy proxies traffic to specifically configured domains enabling conditional access to cloud applications.